Five trillion is a hard number to truly comprehend. But here’s why that’s important.
According to the Ponemon Institute Cost of a Data Breach Report, customer personally identifiable information (PII) is the most sought-after data. Over the two year period between 2018 to 2019, Ponemon found that nearly 33.4 billion customer PII records were exposed due to cloud configuration errors. At an average cost of $150 per exposed PII record, the estimated global cost of these data breaches was in the neighborhood of $5 trillion.
In this article we’ll discuss the importance of proper cloud configuration and cloud management so your company won’t lose money due to cloud misconfiguration.
What is cloud configuration?
Cloud configuration refers to the way you set up the hardware, software, and other elements of a cloud environment. With over four billion internet users worldwide, you have to be sure that your system is easy enough for your customers to access and use. At the same time, it needs to be secure enough to keep unauthorized users from entering areas where they don’t belong.
You can choose from several different cloud types, including:
- Private cloud: All cloud resources are used exclusively by a single business or organization. Resources are typically stored and maintained at an on-premise data center.
- Public cloud: Resources such as servers and storage are owned and managed by a third-party cloud service provider.
- Hybrid cloud: This type of cloud combines the resources from a private cloud with the resources from a public cloud.
Importance of cloud configuration management
Configuring a cloud environment can be complex and challenging—especially when the private and public resources in a hybrid cloud need to communicate and integrate with each other. Because of the complexity, it is vital that you constantly monitor and manage your cloud configuration to make sure it is always up and running and can be accessed as needed.
Fortunately, there are cloud configuration management tools that can help you automate a lot of the testing, provisioning, deployment, installation, and configuration of your infrastructure and software packages to keep your cloud healthy and operating smoothly.
A well-configured cloud environment offers the following benefits:
- Data security: When configured correctly, the cloud’s advanced security features ensure that data is securely stored and handled. Proper security also guarantees that authorized users can easily access the data they need on demand while potential intruders are kept out of your system.
- Scalability: No two companies are alike and they all have different IT needs. There are cloud-based solutions that can easily scale up or down as needed to accommodate fluctuations in demand.
- Automation: You can configure your cloud solutions to update software and systems automatically. This saves time and money and frees up IT professionals to work on other urgent matters. Cloud configuration also allows for automated provisioning, which grants and manages access to cloud-based applications, systems, and data.
- Flexibility: The cloud makes businesses more flexible. When you need more bandwidth, the demand can be managed instantly. There is no need for your IT team to be involved in a complex, expensive, and time-consuming manual update to your infrastructure.
- Control: A properly-configured cloud environment gives you control over sensitive data, letting you easily assign varying levels of access to data and specific documents.
What are the dangers of a misconfigured network?
As smart and efficient as computers and networking systems are, they can’t manage themselves—yet. The default settings that come with the associated hardware and software will not meet all your needs. You still need human interaction with the network to implement custom settings and controls.
And this human interaction is the source of a lot of problems. In fact, a recent joint study by Stanford University and Tessian (a cybersecurity firm) found that 88% of data breaches are caused by human error.
People are prone to mistakes because we simply are not perfect. Fatigue and stress can lead to a simple oversight during the configuration process. That simple oversight can become a major network misconfiguration that can leave your cloud vulnerable to the following malicious attacks from cyber criminals and hackers who just like to wreak havoc.
- Phishing: Fraudulent emails and other communications that look like they come from a reputable source. Sensitive data such as banking, personal identity, and password information can be stolen when the victim opens these types of communications.
- Denial of service: An attack that floods the network with traffic that uses up resources and bandwidth. This renders the system unresponsive to legitimate requests from authorized users.
- Malware: Malicious software such as trojans, worms, and viruses. The goal of a malware attack is to damage the system by spreading malicious software.
- Ransomware: A malware attack that holds data hostage until a ransom is paid.
The bottom line is that cloud misconfigurations can create holes in your network’s security for attackers to exploit. These attacks lead to lost revenue, down time, lost data, and lost customer confidence in your brand.
How do you avoid security misconfiguration?
Every day businesses around the world are hit by cyber attacks. Like an animal trying to find a weakness in a cage, hackers continuously poke at your network looking for vulnerabilities to exploit. Don’t make it easier for them by leaving your network open due to misconfiguration.
It might be impossible to completely eliminate human error, but here are a few suggestions that can help you to significantly reduce them.
Visualize your cloud
Visualizing your cloud setup is key to understanding how all the parts communicate and interact with each other. Lucidchart Cloud Insights can help you create and maintain a map of your entire cloud infrastructure. This visibility gives you insight into expected behavior and data flows, which, in turn, gives you insight into potential configuration problems.
The visibility provided by a map of your cloud can also help you identify and address potential risks such as unnecessary, open administration ports, outbound connections to various internet services, and unsecured, out of date legacy applications communicating with your cloud.
Policies and Training
Because so many misconfigurations are the result of human error, take a more human approach to error prevention. Putting policies and procedures in place and ensuring that your employees are trained to identify potential risks can go a long way to keeping intruders from accessing your system. Some simple things you can do include:
- Practice good password hygiene: Put policies in place that require frequent password updates. Also ensure that employees can’t recycle passwords or use the same password across multiple accounts. The longer the password and the more mixed-case letters, numbers, and special characters used, the better.
- Offer training: The majority of your employees are not experts in network security and rarely think about security issues while doing their jobs. Training can help your employees recognize phishing scams and consider before opening every email. Training can also help employees create strong passwords.
- Block websites and social media: Unless an employee’s job is to monitor social networks, they don’t need to be spending time on Facebook and Twitter at work. Consider locking down social media apps and websites that your employees don’t need to access.
- Implement checks, tests, and validations: Something as simple as marking a checklist can help you avoid configuration errors. Checklists help you focus on details so nothing is overlooked. Testing and validation spotlight problems before they are deployed to the system.
Automation
Many processes and procedures can be completed with automation from a good cloud configuration management tool. Configuration management tools can perform configuration audits to look for signs of unauthorized tampering or changes.
Automation also helps reduce problems that come from human error by blocking suspicious emails, forcing frequent password updates, and so on. Automating network checks, testing, and updates ensures faster deployment, implementation, and scaling.
Even with automation, your system will still need human interaction and monitoring to ensure that everything keeps running, the network is secure, and users can access the data they need. In other words, you need the machines and the machines need you. You have to work together to keep your systems safe from attackers who get more sophisticated and better at their jobs every day.
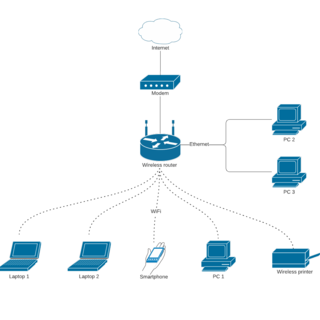
Finally understand how you can use a wireless network diagram to visualize and understand the different components of your network.
Achieve network visibilityAbout Lucidchart
Lucidchart, a cloud-based intelligent diagramming application, is a core component of Lucid Software's Visual Collaboration Suite. This intuitive, cloud-based solution empowers teams to collaborate in real-time to build flowcharts, mockups, UML diagrams, customer journey maps, and more. Lucidchart propels teams forward to build the future faster. Lucid is proud to serve top businesses around the world, including customers such as Google, GE, and NBC Universal, and 99% of the Fortune 500. Lucid partners with industry leaders, including Google, Atlassian, and Microsoft. Since its founding, Lucid has received numerous awards for its products, business, and workplace culture. For more information, visit lucidchart.com.