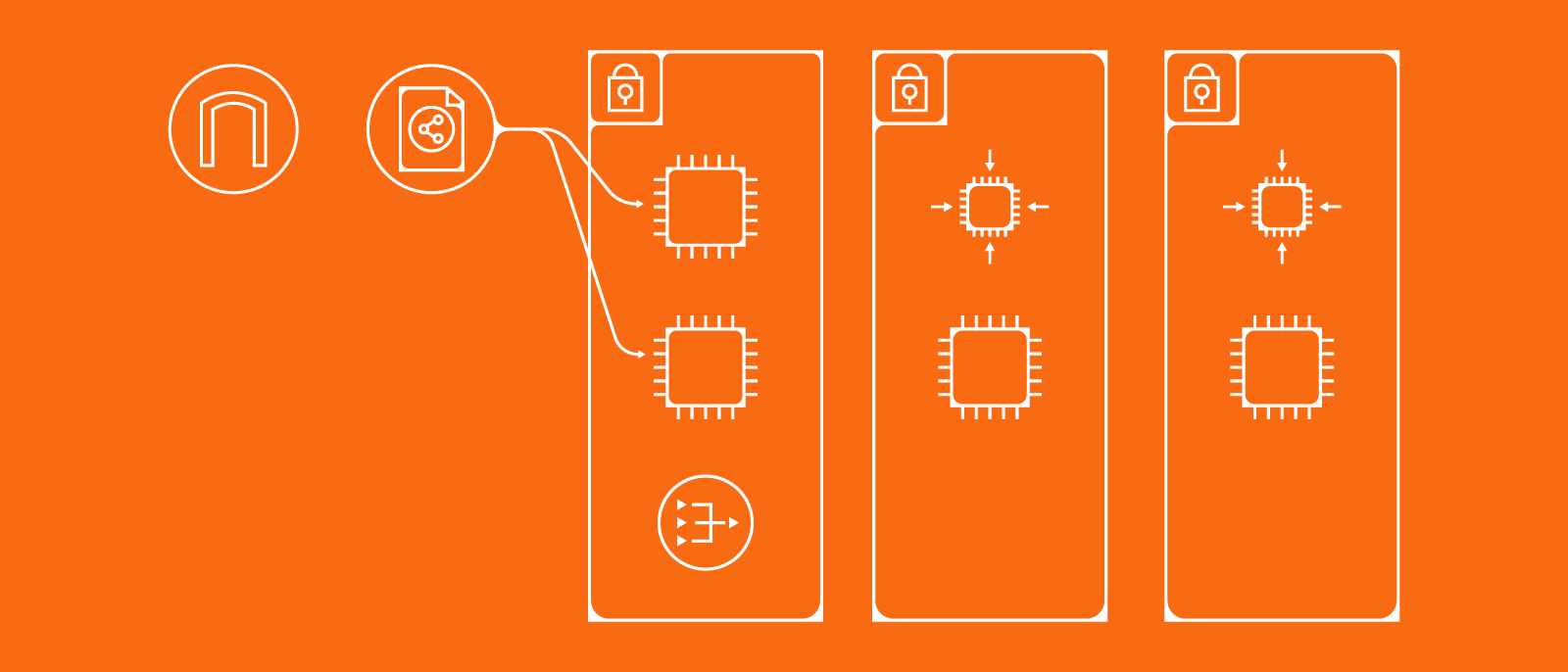
A holistic approach to cloud security can unify your organization against cloud security risks. Setting cloud security policies, implementing best practices, and eliminating silos within your organization allows your team to be more proactive about cloud security.
In this article, we’ll walk you through how to establish a holistic approach to cloud security strategy including how to use visuals to align teams on best security practices and clearly see your cloud environment.
Introduction to cloud security
The average cost of a data breach hit an all-time high at $4.35 million in 2022. And with 45% of breaches being cloud-based, cloud security is an essential investment for enterprise organizations with cloud deployments (which is about 90% of enterprise businesses today). As your organization creates, uses, and manages data, you become vulnerable to security incidents. Unauthorized access to your system is a risk that can significantly damage your company’s business, customers, or reputation (often, security breaches impact all three).
By implementing cloud security best practices, your organization can manage or reduce security risks. Importantly, having cloud visibility helps bring your teams together to collaborate on securing your cloud.
3 pieces of cloud security: Data, networks and people
Let’s dive into the three main components your organization needs to focus on as part of your cloud security strategy: data, networks, and people.
Data
Data protection should be one of your team’s top priorities. Before you can begin improving your data security, you need to take a thorough inventory of your data types.
For instance, your organization may have consumer health information regulated by HIPAA, personal financial data, intellectual property (IP), or corporate data collected through operational activities. Every type of data, depending on its source, contents, and purpose must be managed and protected properly whether the data is at rest or in movement.
Key actions you can take:
- Catalogue your data: Your security team should identify and locate the data (including data connected in shadow IT within your company).
- Know your compliance needs: After knowing what and where your data is, begin outlining your compliance requirements. Find out which regulations apply to your data and what you’re currently doing for data compliance.
Networks
Many IT security teams are genuinely unaware of the full extent of their networks, not because they aren’t trying to gain visibility, but because of shadow IT.
Shadow IT is any IT resource, hardware or software used by a department or individual that isn’t deployed or approved by the IT department. This can include something as simple as a productivity app downloaded by an employee to improve efficiency or work around cumbersome processes.
Whenever employees use IT tools, SaaS, or other computer services your IT team doesn’t know about, it leaves your team unprepared for potential risks and security problems.
Best practice:
- Find your shadow IT: Avoid banning shadow IT outright and, instead, start tracking it. You can use a variety of IT management tools to automatically audit your resources. Then pull that data into Lucidchart to visualize your shadow IT landscape.
People
Even authorized users can contribute to security breaches or the misuse of your cloud system. Clearly defining access and roles, limiting use, and remembering that no system is completely independent of human-error can help your organization manage risks introduced unintentionally by your team (or intentionally by an unauthorized person or for an unauthorized use).
Our suggestion to get your team on board:
- Take a security-minded approach: Create a security plan that is shared with all employees to reduce and account for human error.
4 tips for building a cloud security strategy
As you build your cloud security strategy, keep these four tips top of mind.
1. Gain awareness and visibility of current cloud structure
Before you start building your cloud security strategy, gather all of the information you can on your cloud. Visibility into current cloud architecture should be a priority for your security team.
Cloud APIs can offer security teams the chance to see cloud changes down to the metadata layer. If you aren’t leveraging APIs, your security information could be out of date. Lucidchart can help you visualize complex systems, enabling you to leverage the real-time data generated by your cloud.
- Avoid mapping manually: Mapping your holistic cloud system by hand can introduce errors. Plus, once you’ve created your cloud visualization it is almost immediately out of date. Real-time information is necessary to gain a complete picture of your cloud security circumstances. The best way to ensure you’re always working from accurate information is to automate your cloud visualization.
- Collaborate visually: Go over your cloud structure with your team. You’ll find that this collaboration can actually improve your cloud security.
- Leverage internal and external expertise: Make sure you have the right people reviewing your cloud structure. Your security and information security teams should not be siloed. Similarly, the DevOps team should reference your cloud visuals.
2. Set standards before automation
Standards provide essential automation guidance for your team.
Instead of reinventing the “standards wheel”, find best practices by learning from other security professionals. CIS (the Center for Internet Security) recommends specific standards for cloud security strategies. There are CIS standards for each of the major cloud providers. Robust security platform standards prepare you for automation and help you ensure that your cloud remains secure after you begin the automation process.
The Center for Internet Security recommends these standards:
- Inventory and control of hardware assets: Only use hardware that is authorized by your organization.
- Inventory and control of software assets: Ideally, all software should be known by the IT department.
- Continuous vulnerability management: Whenever you learn of new threats, you should act appropriately to manage them.
- Secure configuration for hardware and software on mobile devices, laptops, workstations, and servers: Ensure that mobile access to your network is secure and set up correctly to protect your networks.
- Controlled use of administrative privileges: Monitor user access to your cloud and track administrative behavior in your system.
- Maintenance, monitoring, and analysis of audit logs: Use audit logs to improve security practices and ensure your organization is protected.
- Email and web browser protections: Reduce the number of opportunities for hackers by making sure all email accounts and web browsers are fully protected.
- Malware defenses: Use automated tools to monitor for malware across workstations and mobile devices.
- Limitation and control of network ports, protocols and services: Manage network vulnerabilities and track network access.
- Data recovery capabilities: Be prepared to recover data if necessary in response to an incident.
- Secure configuration for network devices, such as firewalls, routers, and switches: Manage your network infrastructure security and ensure every department keeps these configurations active.
- Boundary defense: Control the flow of data and understand how information moves in your cloud among various access levels.
- Data protection: Use encryption, protect data integrity, and manage the risk of data loss.
- Controlled access based on the need to know: Align access privileges with roles in the organization.
- Wireless access control: Keep unauthorized wireless devices from connecting to your network. Observe how wireless networking is used within your organization to ensure that improper access is kept to a minimum.
- Account monitoring and control: Follow account lifecycles and remove former employees and contractors from access to your systems.
- Implement a security awareness and training program: Inform your employees about how to protect system security and safeguard data. On a regular basis, update your team about new information, technologies and potential threats.
- Application software security: Patch and upgrade your applications. Use supported versions.
- Incident response and management: Use planning, team training, and careful oversight to ensure you’re prepared for an incident and the immediate aftermath.
- Penetration tests and red team exercises: Test your security practices with pen testing and self-audits.
3. Have security engineers who code on your team
Security engineers in your organization should manage your holistic cloud environments with automation. Since cloud systems are API-driven, you’ll either need to recruit team members who can code and know security or train people you already have.
Having coding expertise is key, even if your organization doesn’t have internal expertise in this area.
- Provide training: Upgrade your team’s security and coding knowledge and you’ll be prepared to move the right people into roles that can protect your cloud.
- Bring on a consultant: If your organization does not have strong coders, consider bringing on a consultant temporarily to help your security team get up to speed with scripting.
4. Establish security in early development
Connect your security team with DevOps to bring security into the development process. Encourage your developers to take a greater role in security so that your security team has allies in your organization’s security efforts.
By embracing security early on in cloud development, you can prioritize cloud security and encourage collaboration throughout the organization. Getting buy-in from developers helps you identify the right points within your cloud to emphasize security and to implement security best practices.
Lucidchart provides teams with a platform for improving visibility and building collaboration on cloud security. Take a deep dive into your cloud structure, look for areas where you can implement improvements, and strategically approach every aspect of your cloud deployment.
With strong visibility of your cloud infrastructure, your team will be able to track benchmarks, verify security decisions, and more effectively protect your cloud.
Visualize your entire cloud infrastructure to build out your cloud security strategy.
Try Lucidscale todayAbout Lucidchart
Lucidchart, a cloud-based intelligent diagramming application, is a core component of Lucid Software's Visual Collaboration Suite. This intuitive, cloud-based solution empowers teams to collaborate in real-time to build flowcharts, mockups, UML diagrams, customer journey maps, and more. Lucidchart propels teams forward to build the future faster. Lucid is proud to serve top businesses around the world, including customers such as Google, GE, and NBC Universal, and 99% of the Fortune 500. Lucid partners with industry leaders, including Google, Atlassian, and Microsoft. Since its founding, Lucid has received numerous awards for its products, business, and workplace culture. For more information, visit lucidchart.com.
Related articles
Top 4 cloud computing security challenges
Learn about the biggest cloud computing security challenges facing organizations today and discover how you can mitigate those risks.
Why single sign-on is essential to business security
Securely managing thousands of accounts and associated user data is a challenge for both users and IT administrators. Single sign-on is one solution organizations use to enhance their IT security, improve user experience, and reduce costs. Learn more.
Bring your bright ideas to life.
By registering, you agree to our Terms of Service and you acknowledge that you have read and understand our Privacy Policy.